Harden Netapp vServer CIFS
CIFS (Common Internet File System) is usually used for file sharing in Windows environments. When running CIFS on a NetApp vServer, security hardening is crucial to prevent unauthorized access and data integrity.
With some simple settings within ONTAP we can fulfill those modern security requirements. Before we can start hardening, on AD-Side several requirements should be already implemented, for example:
- Enabling SMB Signing (GPO)
- Disabling SMBv1
- Forcing LDAPs
- Kerberos authentication
vServer CIFS security
Inspect current security settings
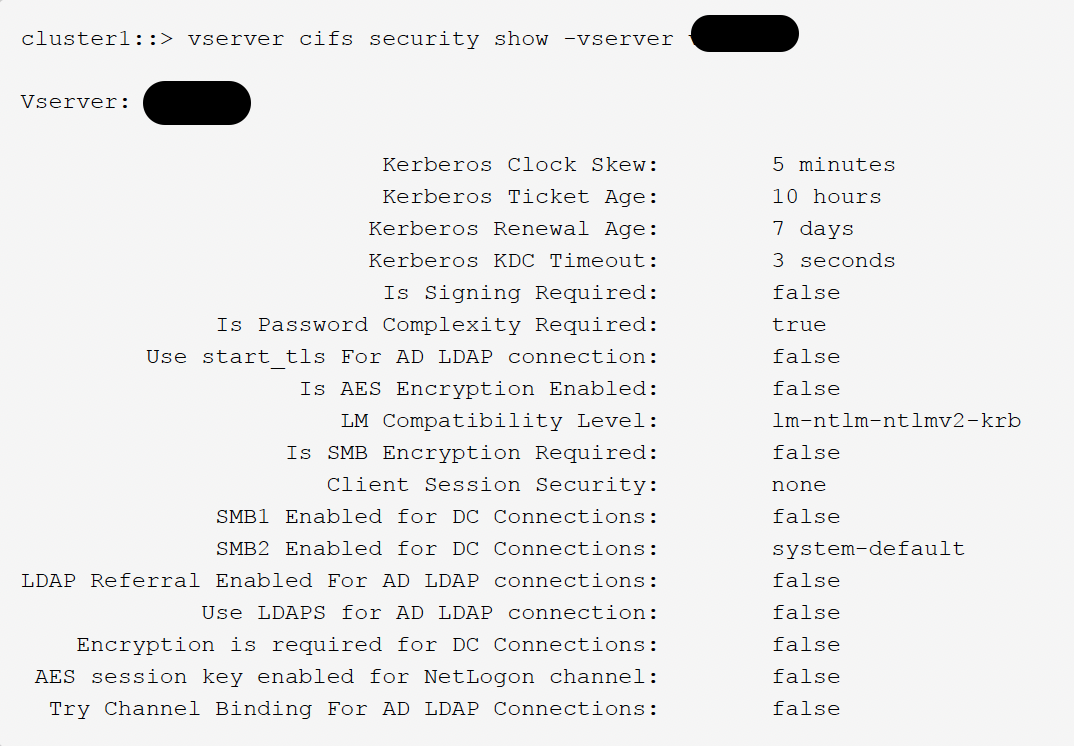
After connecting to our ONTAP Node within ssh, we should at first inspect our current status. Therefore chose a vServer which runs CIFS:
Output (default settings):
LDAPs
I wrote an article about this topic: Enable LDAPS for AD-Integrated Netapp SVM's
SMB Signing
SMB Signing is a security feature that digitally signs SMB packets to verify their origin and authenticity. This prevents tampering and mitigates man-in-the-middle attacks. If enabled, ONTAP accepts SMB messages only if they have valid signatures.
Changes to the encryption settings take effect for new connections. Existing connections are unaffected.
Display information where sessions are signed:
LDAP signing/sealing
Signing LDAP traffic verifies that the packaged data comes from a known source. Signing verifies the integrity of the LDAP payload data through secret key technology, while sealing encrypts the LDAP payload to prevent the transmission of sensitive information in plain text.
ONTAP offers two options:
- Signing
- Signing and Sealing (recommended)
Existing connections will not be impacted by this change.
LDAP channel binding
LDAP channel binding and signing enhance security between LDAP clients and Active Directory domain controllers. However, insecure default settings allow communication without enforcing these protections, creating a privilege escalation risk.
Microsoft advises applying the hardening measures in ADV190023.
Channel binding does have two requirements:
- LDAPs or Start-TSL is enabled
- Session security is set to sign or seal
If those requirements are met, ONTAP tries channel binding by default. Nevertheless we can reenable it (which i would recommend):
LMCompatibilityLevel | Authentication security
You can configure the SMB server's minimum security level (LMCompatibilityLevel) to align with your business security needs for SMB client access. This defines the lowest security token level the server will accept from clients.
- SMB servers in workgroup mode support only NTLM authentication.
- Kerberos is only available if CIFS is domain integrated.
- LMCompatibilityLevel applies only to SMB client authentication, not administrative authentication.
- Four security levels are available for minimum authentication settings.
- lm-ntlm-ntlmv2-krb (default)
- ntlm-ntlmv2-krb
- ntlmv2-krb (Recommended, ONTAP will force Kerberos if it fails it will fall back to ntlmv2)
- krb (Kerberos only)
Ensure your Clients connection while using the DNS-Name, due to Kerberos authentication! Your DNS should be set up properly.
Kerberos AES encryption
For maximum security in Kerberos-based communication, enable AES-256 and AES-128 encryption on the SMB server. Beginning with ONTAP 9.13.1, AES encryption is enabled by default.
The SMB server supports the following Kerberos encryption types: - AES-256 - AES-128 - DES - RC4-HMAC
For maximum security, enable AES-256 ncryption on the SVM:
In earlier ONTAP versions (9.13.1) the administrator is prompted to enter the administrative AD credentials for the OU containing the SMB server.
Encrypt communication to DCs
Make sure your Domain Controllers supports SMB v3 (this is meanwhile state of the art..) because SMB encryption only negotiates with SMB v3 connections. If a DC does not support SMB v3, ONTAP will not connect to it.
SMB Encryption (use with caution)
Make sure that all requirements are met for SMB Encryption in your environment. Windows clients beginning with Windows Server 2012 and Windows 8 support SMB encryption.
SMB encryption on the SVM is managed through two settings:
- An SMB server security option enabling encryption on the SVM.
- An SMB share property controlling encryption per share.
You can enforce encryption for all SVM data or only for specific shares. SVM-level settings override share-level configurations.
This is how to setup encryption on SVM level:
SMB encryption increases CPU usage on both Windows clients and the server, impacting performance, though network traffic remains unchanged.
Changes to the encryption settings take effect for new connections. Existing connections are unaffected.
References
docs.netapp - Configure and enable CIFS SMB signing and sealing
docs.netapp - Microsoft Security Advisory: ADV190023
docs.netapp - Overview of using LDAP
kb.netapp - Which ONTAP version allows to enable LDAP channel binding
docs.netapp - Set the SMB server minimum authentication security level
docs.netapp - Performance impact of SMB encryption
docs.netapp - SMB encryption overview
Cheers!
